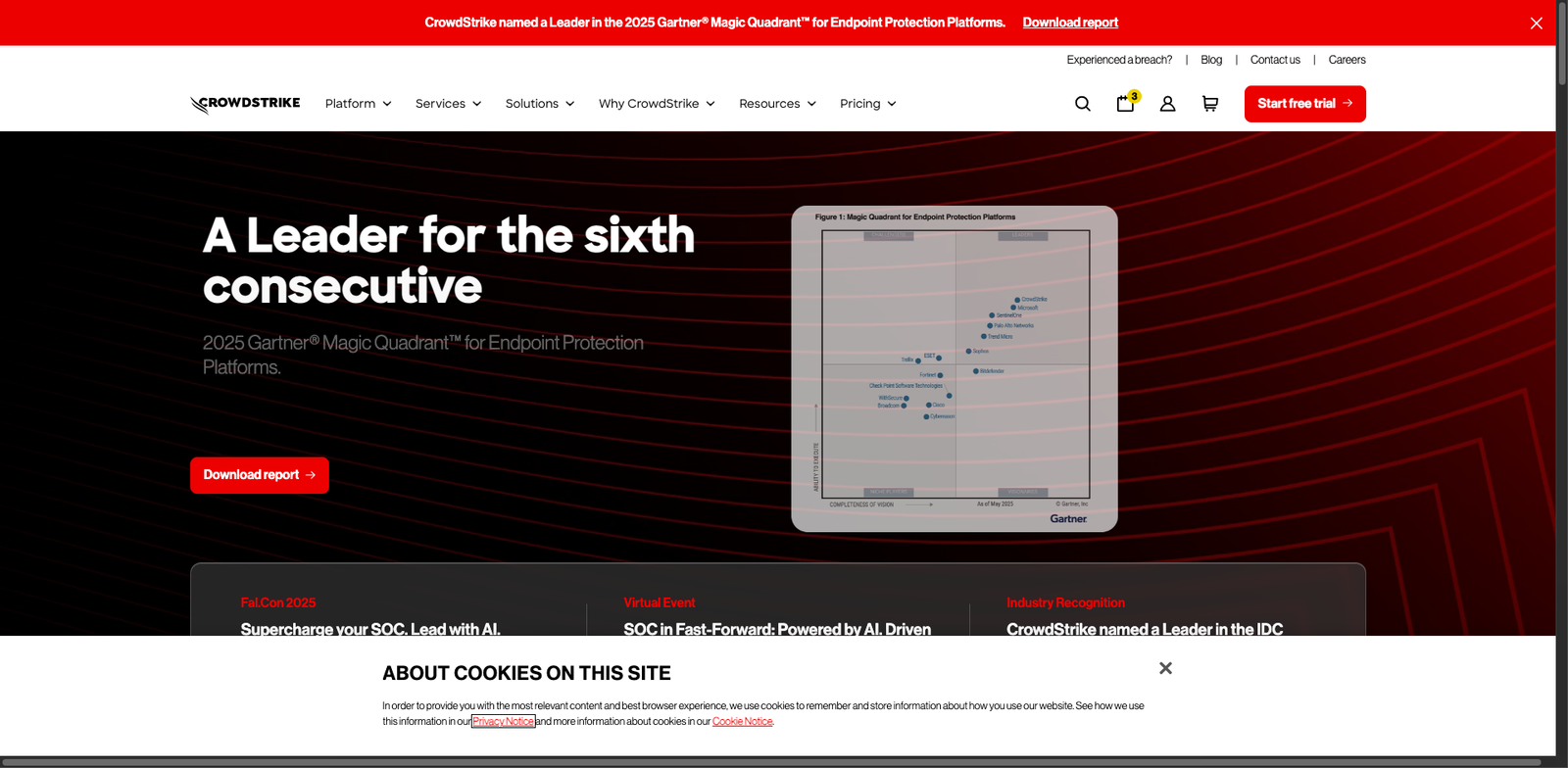
VirusTotal Enterprise provides comprehensive threat intelligence and attack surface monitoring. It helps organizations identify and mitigate security risks efficiently.
Key features
- Advanced threat analysis capabilities
- Customizable reports and dashboards
- Integration with other security tools
- Real-time monitoring and alerts
- Collaborative features for team-based investigations
Pros
- High accuracy in threat detection
- User-friendly interface
- Strong community and support
- Regular updates with new threat data
Cons
- Pricing details are not publicly available
- Limited features in lower-tier plans
- Potential steep learning curve for new users